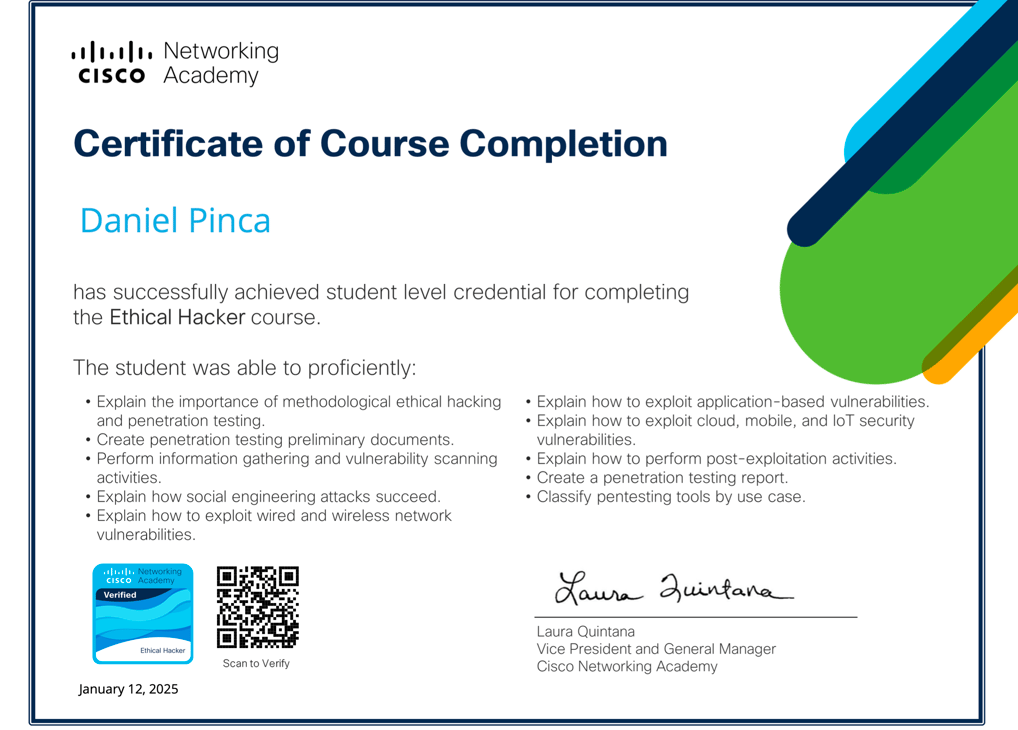
Passionate about securing digital systems, I specialize in penetration testing, vulnerability assessments, and ethical hacking to identify and mitigate security risks. With expertise in offensive security, network defense, and exploit development, I leverage industry-leading tools and methodologies to strengthen organizational defenses.
🔹 Technical Skills:
✔ Penetration Testing & Ethical Hacking – Skilled in network and web application security, exploit development, and social engineering attacks.
✔ Vulnerability Assessments – Proficient in bug detection, risk analysis, and security testing methodologies.
✔ Offensive Security & Red Teaming – Hands-on experience with Metasploit, Burp Suite, Nmap, Wireshark, and custom exploit scripting.
✔ Defensive Security & Incident Response – Expertise in security monitoring, forensic analysis, and threat mitigation.
✔ Secure Software Development – Strong understanding of secure coding practices, encryption techniques, and secure authentication mechanisms.
🔹 What I Bring:
✅ A hacker mindset with a commitment to ethical security practices.
✅ Deep knowledge of cyber threat landscapes, social engineering tactics, and security hardening techniques.
✅ Passion for continuous learning and staying ahead of emerging cyber threats.
I’m driven to protect organizations from evolving cyber threats and collaborate with security teams to enhance defenses. Let’s connect and secure the digital world together! 🔐🚀
Ethical Hacker